
Data breach insurance
Data breach insurance safeguards businesses from the costs of a data breach or other cyber threats. Several insurance policies offer protection to cover data-breach related costs, such as client lawsuits and security fixes.
What is data breach insurance coverage?
Data breach insurance coverage refers to several different policies that all safeguard the same part of your business: information. This insurance helps you respond to a breach if sensitive information gets lost or stolen – from a hacker's phishing attack on your network or a lost employee laptop with unencrypted data.
These policies include data breach insurance, cyber liability insurance, and technology errors and omissions insurance (tech E&O).
Why is data breach coverage important?
Any business that works with or handles sensitive or personal data can be a target for an expensive data breach. Generally, data falls into one of two categories: personal information and financial information. And, if you store either types or transact online, your business is at risk.
As security breaches become more common, the financial strain will also increase. Small business owners aren't likely to afford the cost of a data breach out of pocket. But with data breach insurance coverage, they're able to easily recover from the financial losses associated with a cyber attack.

Who needs data breach insurance coverage?
Small businesses are attractive targets for data breaches, ransomware attacks, and other cyber incidents. They often lack the resources and security to either fend off or minimize a breach. Unfortunately, it’s also more difficult for small businesses to recover, with about 60% of small businesses closing within six months of experiencing a cyberattack.
Businesses that would most benefit from data breach coverage fall into three main categories:
- Companies that store customer information like credit card, Social Security, or bank account numbers. This includes online retailers, accounting firms, and many other businesses.
- Companies that handle personal health information, like medical offices, chiropractors, and physical therapists.
- Any IT or technology business – especially professions like cybersecurity, network security, software developers, web hosting, or app developers.
Top industries we insure
Don't see your profession? Don't worry. We insure most businesses.

How much does data breach insurance cost?
The premium for data breach insurance is quite low when you consider how much a data breach could cost your company. The amount you pay depends on the type and amount of coverage you buy. For example:
Adding a data breach rider to your general liability policy is the least expensive option. It should only add a small amount to your general liability insurance premium. Small businesses pay an average cost of $42 per month for this policy.
Purchasing a standalone cyber insurance policy costs an average of $140 per month for Insureon's small business customers.
Bundling coverage in a tech E&O policy costs an average of $60 per month for small IT and technology businesses.
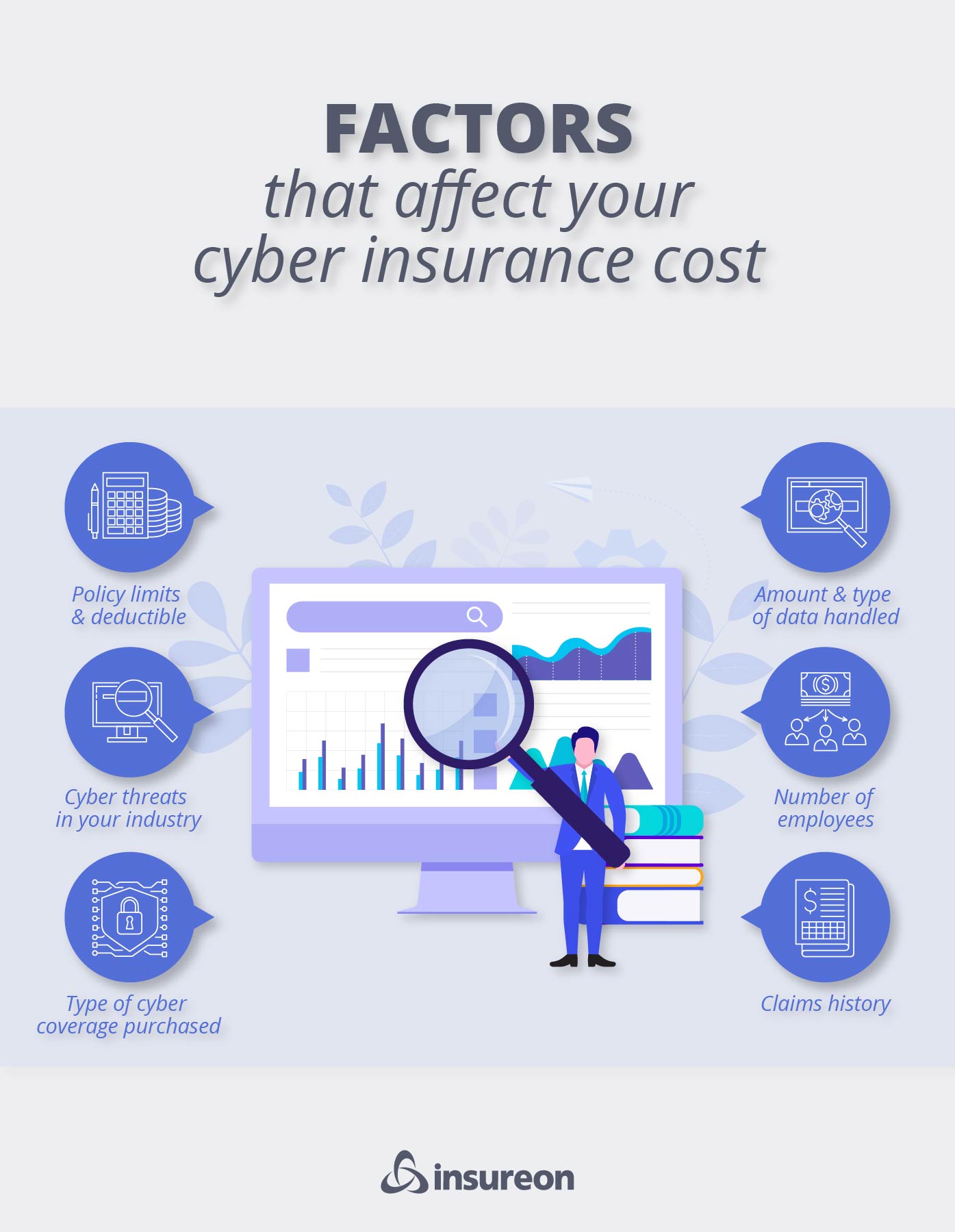
In addition to the type of coverage you buy, these factors also affect your premium:
- Your policy limits
- The amount of sensitive data your company handles
- Your business size and revenue
- Your claims history
What are the types of data breach insurance?
Commonly referred to as cyber liability insurance, data breach insurance helps cover the costs of cybersecurity breaches. The type of data breach insurance your business needs depends on the type of work you do and how much cyber risk you face.
For instance, a web hosting company would need broader data breach insurance coverage than a medical office. While both businesses handle customer data, the web hosting company could be held liable for a data breach that affects its clients.
There are four different options for data breach insurance to choose from, depending on your coverage needs:
- First-party cyber liability insurance
- Third-party cyber liability insurance
- Technology errors and omissions insurance
- A data breach insurance rider to general liability insurance or a business owner’s policy (BOP)
What is first-party cyber liability insurance?
First-party cyber liability insurance protects you from the high costs of a data breach or ransomware attack against your business’ servers and computer systems. If your business stores sensitive data like credit card numbers or Social Security numbers, you should consider first-party coverage.
This insurance policy will protect you from the damaging costs of a data breach, such as:
- Investigating and correcting the cause of the breach
- Business interruption
- Customer notifications
- Fraud and credit monitoring services
- Cyber extortion negotiation and demands
- Regulatory fines
- Public relations efforts
What is third-party cyber liability insurance?
Third-party cyber liability insurance protects you from lawsuits related to financial losses from a data breach or other cyber incident at your client’s business.
Any business that could potentially be blamed for a client’s data breach may need this coverage, such as cybersecurity companies, network security companies, software developers, or IT consultants. It's a must-have for anyone responsible for a client's cybersecurity, even if they only recommend software.
Regardless of fault, third-party coverage can help pay costs like:
- Attorney’s fees
- Settlements and judgments
- Court costs
What is technology errors and omissions insurance?
Many IT businesses choose to purchase a technology errors and omissions insurance policy, which combines third-party cyber liability insurance with errors and omissions insurance – often at a discount.
Tech E&O insurance protects businesses from lawsuits over the quality and delivery of your work. It provides liability coverage related to:
- Client data breaches and cyberattacks
- Work mistakes and oversights
- Undelivered services
- Missed deadlines
- Accusations of professional negligence
What is a data breach insurance rider to a general liability policy or BOP?
Data breach insurance may be available as a rider (add-on) to your general liability insurance or business owner’s policy. This is a good option for businesses that have lower cyber risks and store limited amounts of sensitive information.
Be cautious, though – data breach riders typically come with smaller limits than their full policy equivalents. If you’re unsure of what level of data breach coverage you’ll need, one of our expert insurance agents can help.
What types of data breaches are covered?
Data breach insurance covers both accidental and intentional data breaches due to:
- Employee errors
- Software and security flaws
- Cyberattacks like hacking, malware, and ransomware
- Employee data theft
However, not all data breach insurance policies cover every situation.
For instance, a first-party cyber liability policy would cover you if one of your employees opens a phishing email. It won’t protect you if you’re sued by a client because a software company you recommended accidentally exposed their data. In that instance, you would need third-party cyber liability coverage.
Other common questions about data breach insurance
What's the cost of a data breach?
A study from the IBM | Ponemon Institute found that data breaches cost businesses $242 per stolen record on average. That means a small business that stores data on 1,000 customers could expect to spend nearly a quarter of a million dollars recovering from a breach.
The actual cost will depend on several factors, including:
- How many people were affected
- The cost of finding and fixing the cause of the breach
- Any cyber extortion demands
- How long your business was interrupted
- Lost business due to reputation damage
- Regulatory fines and penalties
Without the right business insurance and protections in place, a data breach could do serious damage to your business and your bottom line. A data breach insurance policy can cover all of these costs and get you back to business as usual.
What does data breach insurance not cover?
To fully understand what your data breach insurance policy does and doesn't cover, you should read the fine print in detail. But typically, data breach insurance does not cover third-party data theft. In other words, your business isn't covered if you happen to cause someone else’s data to be breached. It only covers financial losses your business incurs when dealing with an attack on your company.
Other exclusions from data breach insurance coverage include:
- Data loss caused by accidental damage. A data breach policy covers information lost in a software attack, but doesn't insure data lost from physical damage to a network or storage device. An electronic data liability policy expands your property damage coverage to include a loss of data caused by accidental damage.
- Data loss from natural occurrences. If sensitive data is lost because of a fire, flood, power surge, or other natural disaster, you'd need electronic data processing (EDP) insurance. This provides protection for data loss due to your equipment, such as computers and backup systems.
Save money with cyber insurance quotes from Insureon
Complete Insureon’s easy online application today to get quotes from top-rated U.S. insurance companies. Once you find the right policy for your small business, you can begin coverage in less than 24 hours.
